Defcon 25
Burner phone? Check. Laptop wiped? Check. Few WN722N adapters? Check.
It was that time of year again, where the InfoSec community got together in Las Vegas for the world’s largest hacking conference, with an estimated 25,000 people, for three day of: talks, hacking and drinking.
Talks
Defcon has been running every year since 1993, back from the days of BBS, usually surrounded by controversy in the news.
This year was no exception, with the main controversy surrounding (American) voting machines, owned and exploited within minutes to hours [1]. A few interesting talks from this year included:
-
Abusing webhooks for command and control [2] – a demonstration of using web hooks in common continuous integration and build management platforms, such as Github Enterprise (used at Worldpay), to create backdoor tunnels to transfer files and run commands from within a secure/hostile network. All wrapped up in a simple tool, requiring only a malicious branch to be pushed up in any repository, with network activity looking like that of a developer. This just shows the importance of protecting our accounts from phishing and socially engineering, as any developer could open the gate to our entire infrastructure.
-
JSON Attacks! [3] – remember the serialization vulnerabilities from Apache Commons in 2015 [4]? The new word on the block is JSON libraries, with almost every popular library vulnerable in some form, except Gson (Java).
-
Exploiting URL Parser in Trending Programming Languages [5] – probably my favourite talk from this year. Due to inconsistencies between URL parsers/validators and requesters, various languages and libraries (Python, .NET, Java, etc) can be tricked into retrieving dangerous URLs. An example was demonstrated for Github.com, where the speaker was able to chain another exploit for remote code execution, using a malicious webhook URL. Subsequently files could be pulled off a server and network belonging to Github.com. This meant Github Enterprise was also vulnerable, as it’s the same application.
-
Application DOS in Microservice Architectures [6] – a talk by security engineers at Netflix, a company well known for pushing micro-services in the industry. This talk looks into methods of denial of service, through expensive API calls, and ways to mitigate these attacks. The team successfully managed to take down a region of Netflix for 5 minutes using AWS, and a custom open-sourced tool, costing a massive…$1.71.
-
Wiping out CSRF [7] – a look at CSRF in 2017, as well as a few prevention techniques in legacy applications through JavaScript.
-
DOOMed point of sale systems [8] – when a Verifone payment terminal is left with the default password for an admin screen, which is more common than you’d think, it took this speaker only a few vulnerabilities to run a classic game of DOOM on it.
Images
Some of my own images, although my burner phone’s camera was a bit rubbish:
-
 Packet Hacking Village
Packet Hacking Village -
 Main Esculators
Main Esculators -
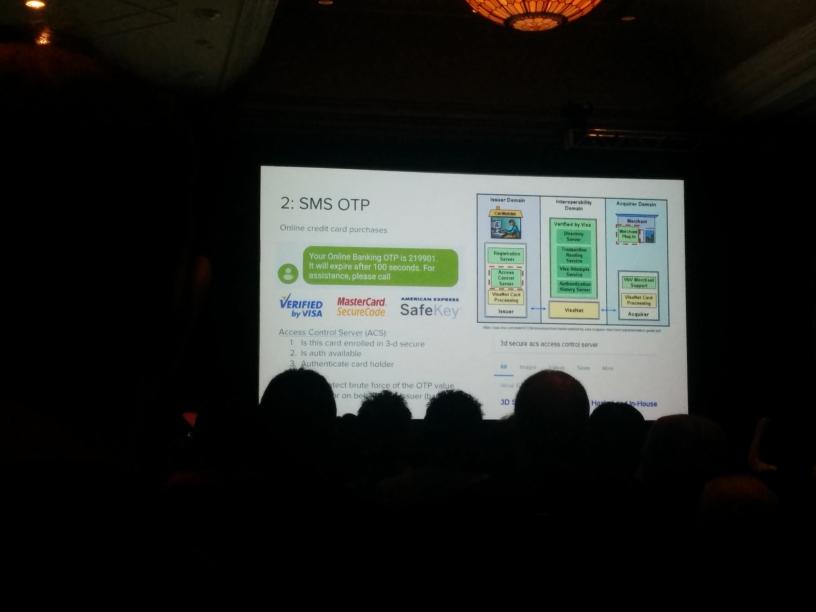 Quick snap from a talk on defeating SMS One Time Password (OTP) with brute force
Quick snap from a talk on defeating SMS One Time Password (OTP) with brute force
Few pictures taken from public domain:
Next Year
Defcon is cancelled [9].
References
- https://www.theregister.co.uk/2017/07/29/us_voting_machines_hacking
- https://media.defcon.org/DEF%20CON%2025/DEF%20CON%2025%20presentations/DEFCON-25-Dimitry-Snezhkov-Abusing-Web-Hooks-UPDATED.pdf
- https://media.defcon.org/DEF%20CON%2025/DEF%20CON%2025%20presentations/DEFCON-25-Alvaro-Munoz-JSON-attacks.pdf
- https://blogs.apache.org/foundation/entry/apache_commons_statement_to_widespread
- https://www.blackhat.com/docs/us-17/thursday/us-17-Tsai-A-New-Era-Of-SSRF-Exploiting-URL-Parser-In-Trending-Programming-Languages.pdf
- https://media.defcon.org/DEF%20CON%2025/DEF%20CON%2025%20presentations/DEFCON-25-Scott-Behrens-and-Jeremy-Heffner-Starting-The-Avalanche-Application-DoS-In-Microservice-Architectures.pdf
- https://media.defcon.org/DEF%20CON%2025/DEF%20CON%2025%20presentations/DEFCON-25-Joe-Rozner-Wiping-Out-CSRF.pdf
- https://media.defcon.org/DEF%20CON%2025/DEF%20CON%2025%20presentations/DEFCON-25-trixr4skids-DOOMed-Point-of-Sale-Systems-UPDATED.pdf
- https://motherboard.vice.com/en_us/article/ezvez4/def-con-is-cancelled-again

 The Less Busy Esculators
The Less Busy Esculators  Main Conference Hall
Main Conference Hall  Cool Antenna Hack
Cool Antenna Hack
Comments